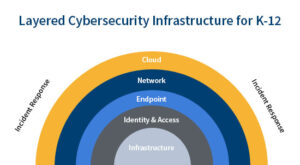
Putting together a cybersecurity strategy is a lot like growing onions. If it doesn’t have layers, you’re probably doing it wrong.
Of course, we’re talking about multi-layered cybersecurity. With more school districts taking a renewed interest in data protection, many are looking high and low for new ways to keep student privacy safe. Luckily, that’s exactly what a layered approach to cybersecurity is all about.
In this blog, we’ll explain the basics of multi-layered protection and why your school district stands to gain from an additional layer of cloud security.
WHAT IS MULTI-LAYERED CYBERSECURITY?
A multi-layered cybersecurity strategy uses multiple layers of defense to protect sensitive data from potential threats, such as malware, ransomware, or a phishing attack.
Each layer provides a different level of protection, fulfilling its own specific data security function. These multiple layers work in combination to create a comprehensive and effective cybersecurity posture.
By taking a layered approach, you can protect the entire attack surface from unauthorized access or exposure. In simpler terms, it allows you to cover all the bases simultaneously.
HOW DOES MULTI-LAYERED SECURITY WORK?
If you want to understand the value of multi-layered threat protection, it’s best to put it into context.
According to Forbes, a traditional security strategy generally involves designing a defensive perimeter around your most sensitive data. Preventative tactics like this are crucial to safeguarding assets from conventional attack vectors, but tend not to account for internal threats like an accidental leak.
A layered approach works more proactively. It implements various types of data security controls at different levels of your IT infrastructure. For example, multi-layered cybersecurity could include firewalls, data loss prevention tools, endpoint security, or access controls. Because each layer is designed to detect and prevent different types of threats, they work together to create a holistic security framework.
Notably, this multi-layered approach is similar to “defense in depth,” a strategy that also uses multiple layers of controls to mitigate cyber threats. However, a defense-in-depth strategy typically focuses security operations on a single layer of the infrastructure (e.g., the device or network), whereas multi-layered security focuses on the entire technology stack.
Contact your dedicated Account Manager:
David Waugh
Sales and Marketing Vice President
303-415-3643
dwaugh@managedmethods.com
